Policy Implementation, Enforcement, and Compliance HIC, Inc. needs to maintain
Month: June 2024
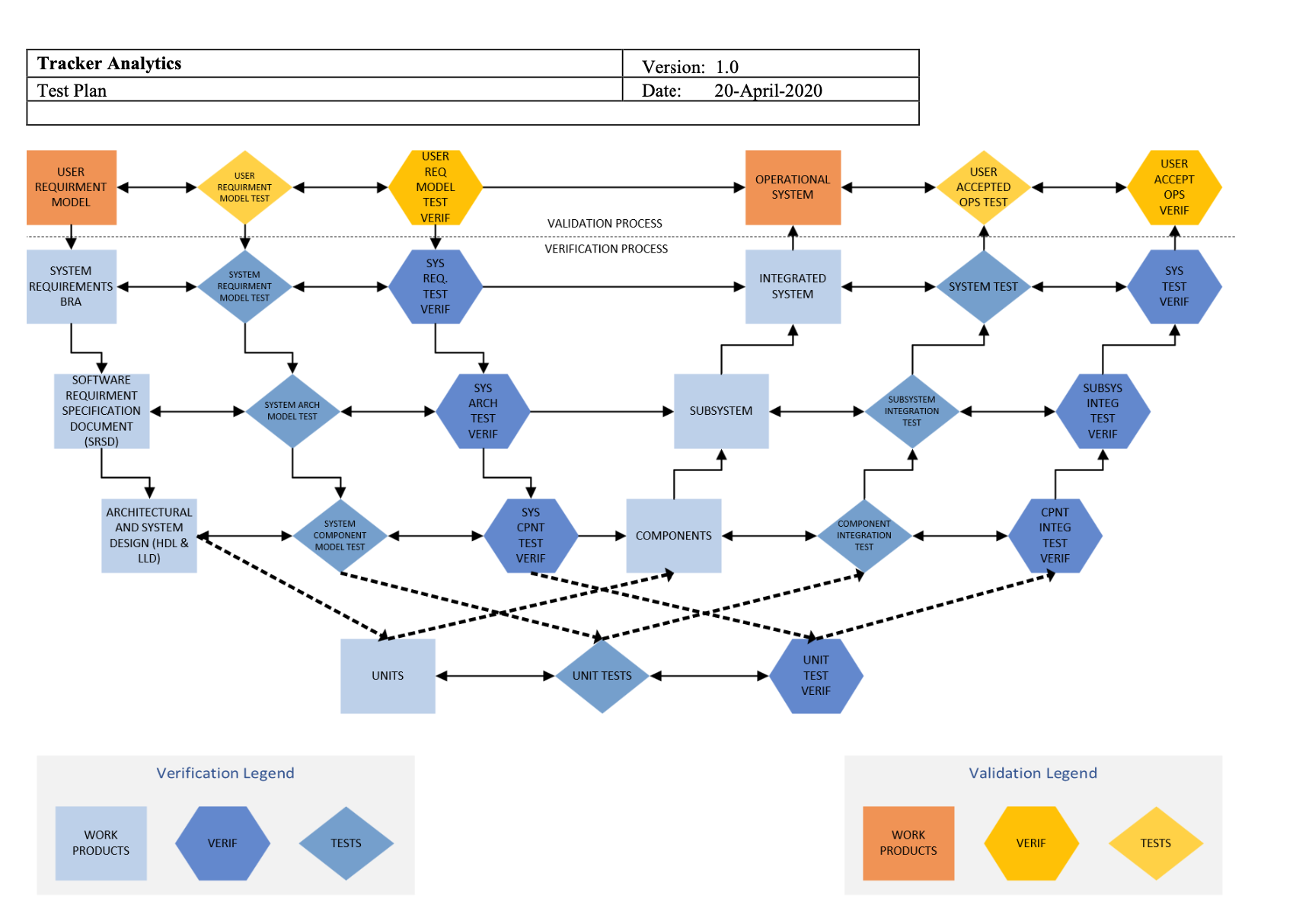
Secure Software Design and Development A Software Development Life Cycle
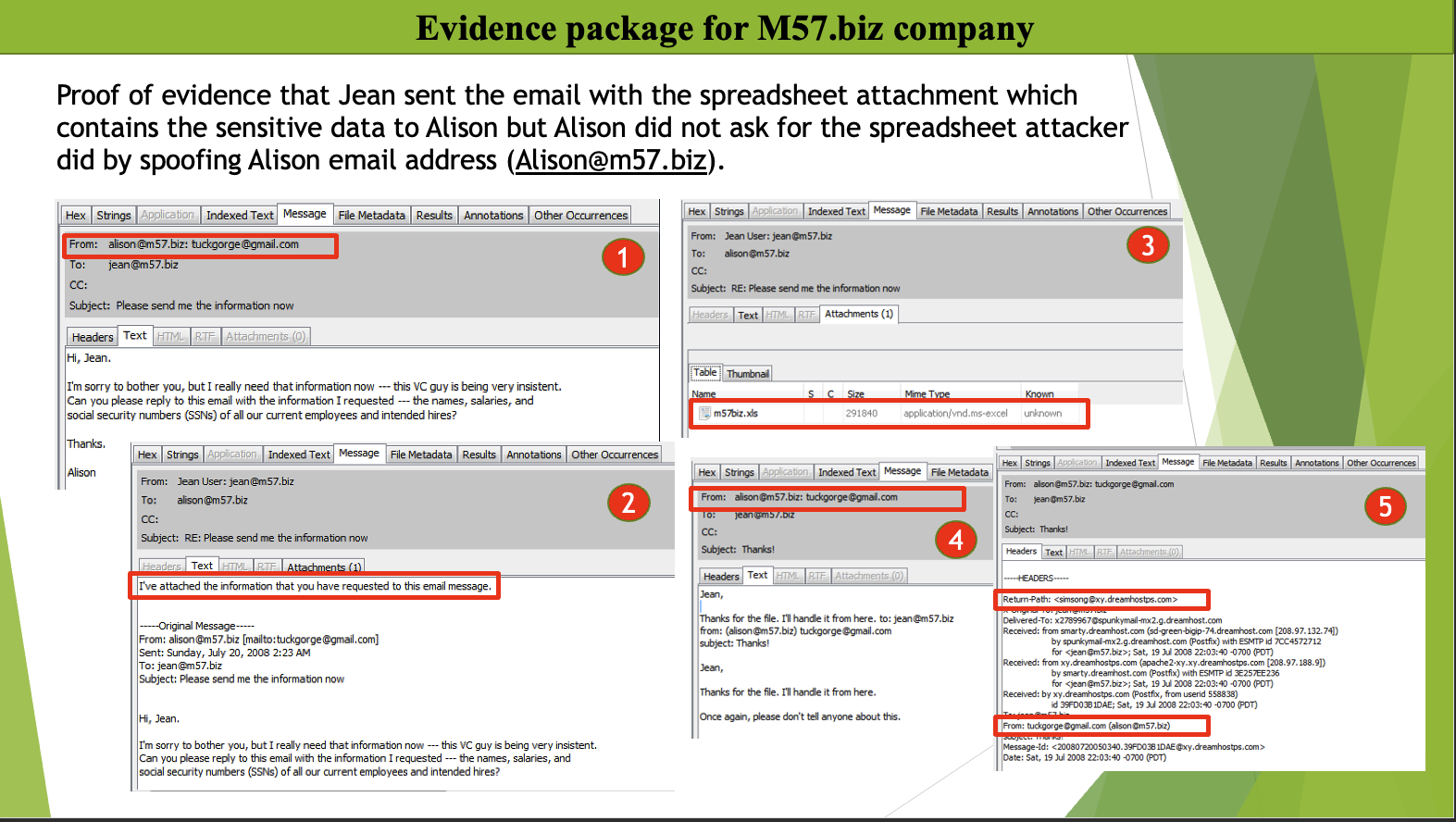
Incident Response and Computer Network Forensics Every organization in today’s
Privacy Policies HIC, Inc. has three privacy domains – PHI,

Risk Management The fundamental goals of cybersecurity are to manage
