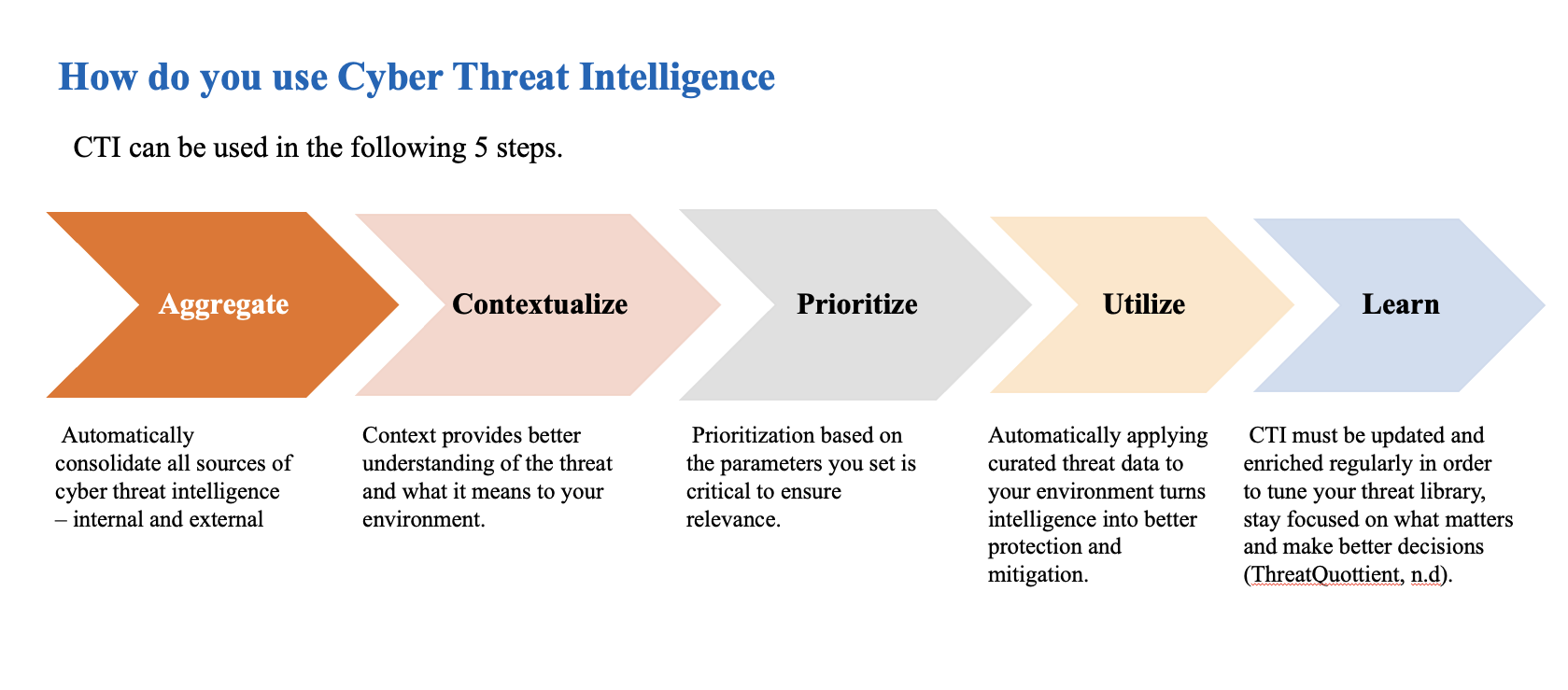
Cyber Threat Intelligence
The Cyber Threat Intelligence (CTI) examines the fundamentals of open source intelligence, refining the information into actionable intelligence, and the basics of the intelligence cycle with particular emphasis on anticipating threats to the cyber domain. The CTI can be broken into three types of threat intelligence (TI): Strategic, Tactical, and operational. The strategic focus on threat actors, their intentions, motivations, and capabilities. The tactical focus on tactics, techniques, and procedures of threat actors. The operational centers on determining if a threat actor is planning to engage your organization, or has already breached by looking through network logs and collected data (Giandomenico, 2017).
Any sort of threat intelligence is simply assessed information, and can only be understood in the context within which it is created and the proposed purpose of its use. The purpose is usually to increase awareness of defined situations and environments and to aid in decision-making, at either an operational, tactical or strategic level (Ernst & Yong. n.d.)
I chose my final project Cyber Threat Intelligence Plan (CTIP) as my artifact to demonstrate my understanding of cyber threat intelligence, and how it can be applied to an organization. For the project, I chose NetStore as my company and addressed their threat actors and method of delivery. The Cyber Threat Intelligence enables NetStore to become better informed about the types of attacks they face, proactively defend against those attacks, and manage enterprise data and transactional risk more e!ectively (Hancock, Anthony, & Ka!enberger, 2015).
Reflection
NetStore’s business is to provide secure devices and services to its private and public sector customers. NetStore must protect its servers, network components, user devices, people, network and system design specifications, and VPN configurations. Threat actors usually look for critical information such as intellectual property (IP), product development, manufacturing processes, business plans, policies, emails, organization charts, user credentials, supply chain, and partner networks.
In my final project, I discussed the threats, threat actors, and methods of delivery challenging NetStore. The five types of threat actors that addressed in the paper are Cybercriminals, Competitors, and Cyber Espionage Agents, Insiders, Opportunistic,and Internal User Errors.
My knowledge about cyber intelligence before was minimal, but after going through this program, I understand why organizations must have well-defined cyber threat intelligence. There is a lot to learn in this field. In my opinion, this program gave us the knowledge on how to conduct open-source intelligence, how to sources good vs. bad information, how the cyber kill chain can be used to mitigate a cyber-attack. I did also learn how to write briefings and create a presentation for C-level executives about the threats, threat actors, and mitigation.
References
- Ernst & Young. (n.d). How do you find the criminals before they commit the cybercrime? Retrieved from https://www.ey.com/Publication/vwLUAssets/EY- how-do-you-find-the-criminal-before-they-commit-the- cybercrime/%24FILE/EY-how-do-you-find-the-criminal-before-they- commit- the-cybercrime.pdf
- Giandomenico, A. (2017, June 27). Know your enemy: Understanding Threat actors. retrieved from https://www.csoonline.com/article/3203804/know-your-enemy- understanding-threat-actors.html
- Hancock, G., Anthony, C., & Ka!enberger, L. (2015, December). Tactical Cyber Intelligence. Retrieved from https://ole.sandiego.edu/bbcswebdav/pid-1350644- dt-content-rid-15084225_1/xid-15084225_1
Cyber Security Fundamentals related links