Policy Implementation, Enforcement, and Compliance HIC, Inc. needs to maintain
Author: naveen
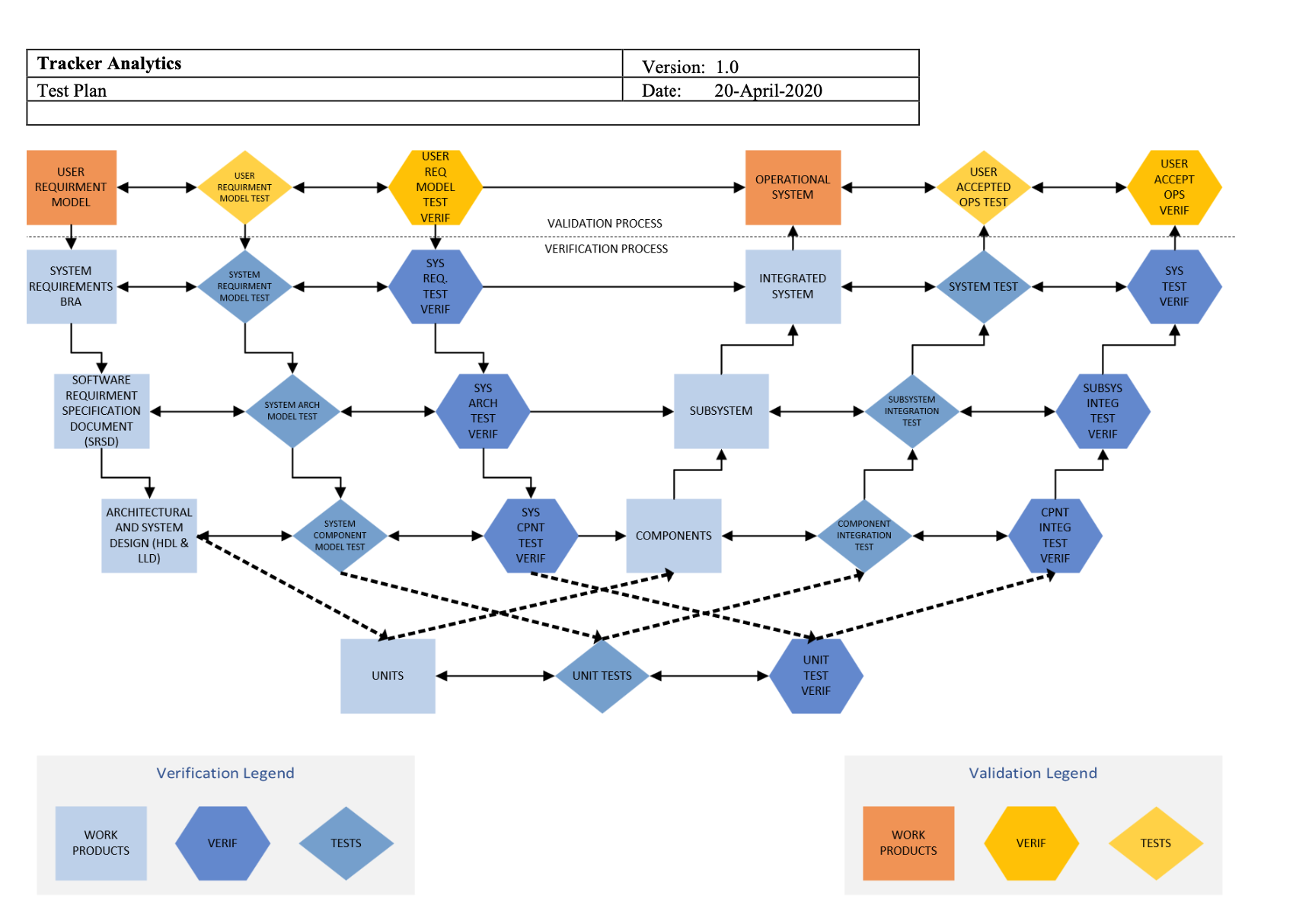
Secure Software Design and Development A Software Development Life Cycle
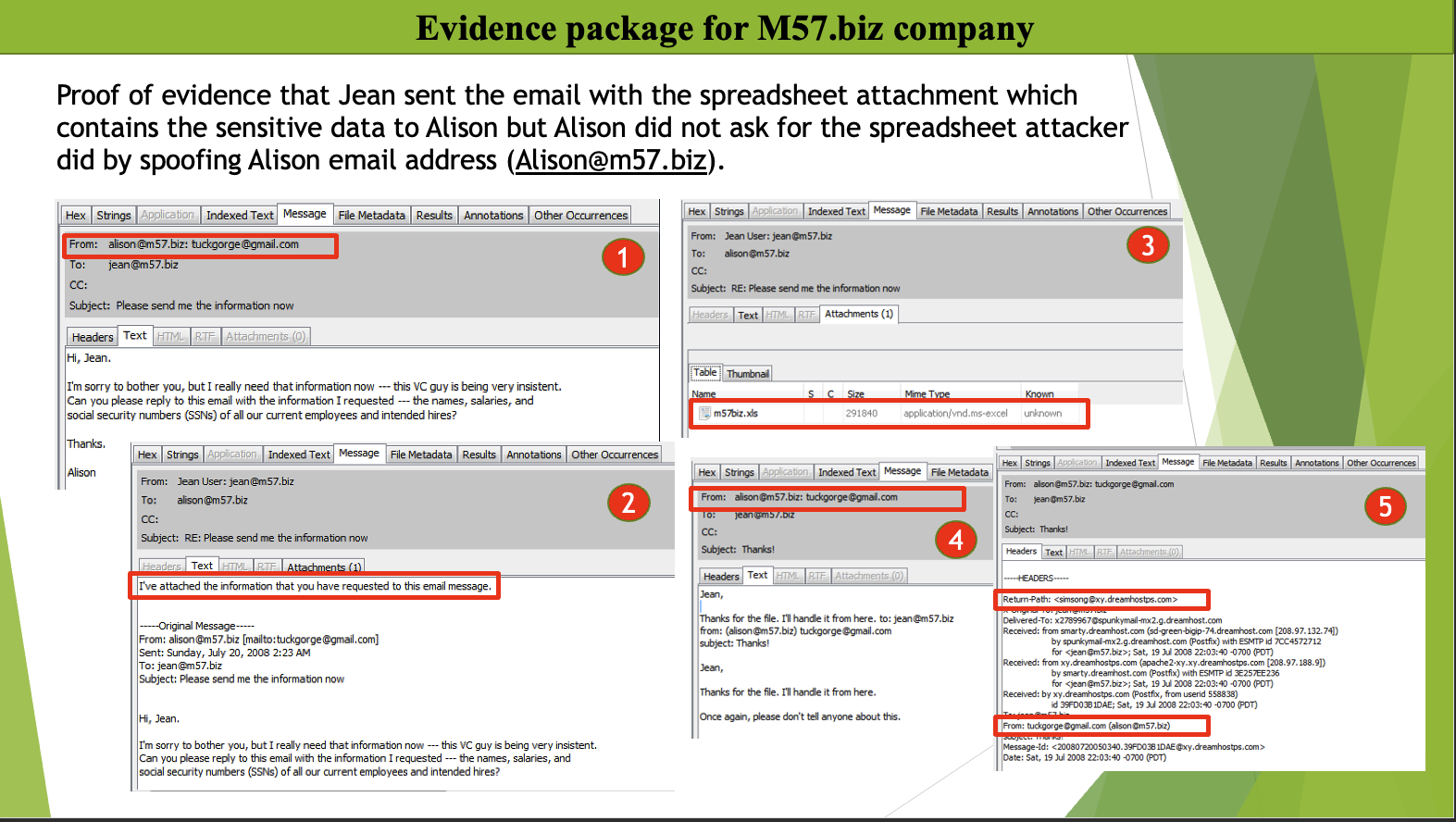
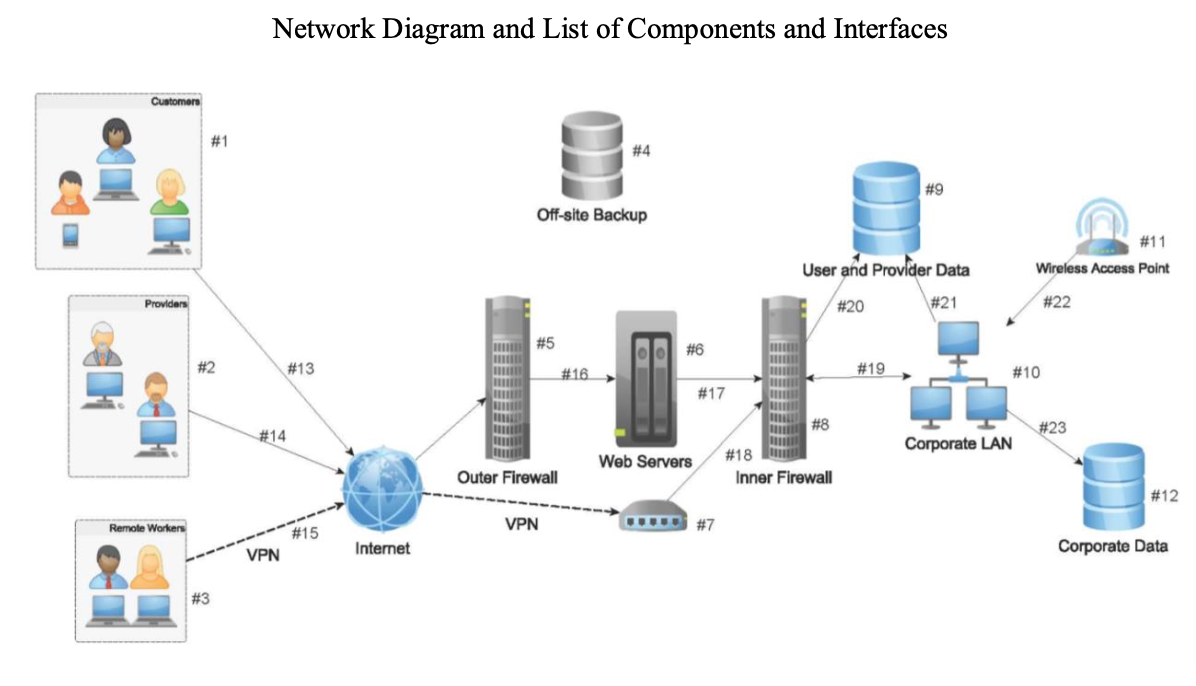
Incident Response and Computer Network Forensics Every organization in today’s
Privacy Policies HIC, Inc. has three privacy domains – PHI,

Risk Management The fundamental goals of cybersecurity are to manage
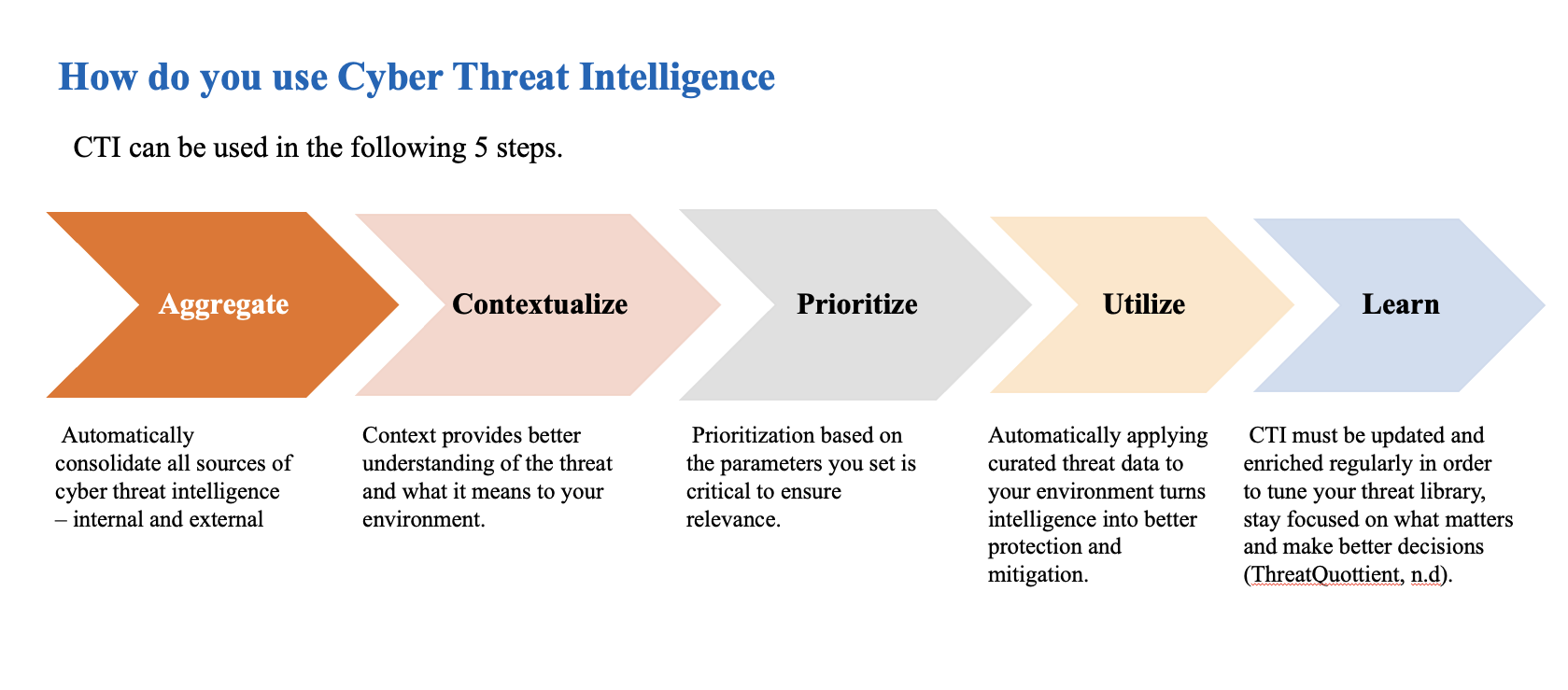
Cyber Threat Intelligence The Cyber Threat Intelligence (CTI) examines the
Cryptography Cryptography is art and science that applies complex mathematics
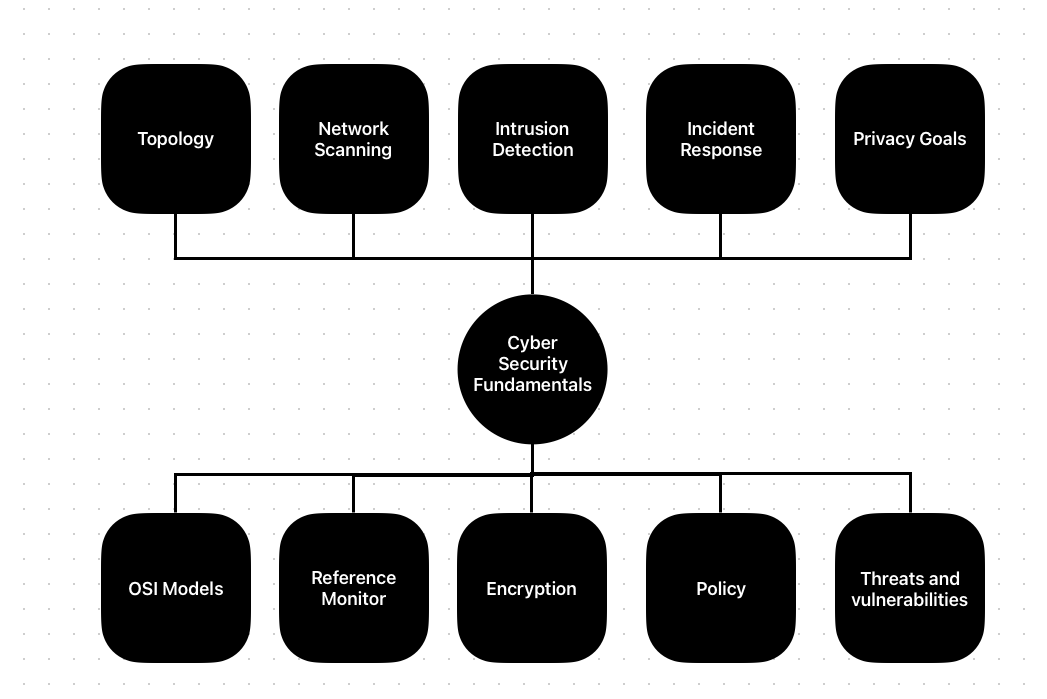
Cyber Security Fundamentals The progression of computers and information technology
When I try to publish my posts from Ulysses application
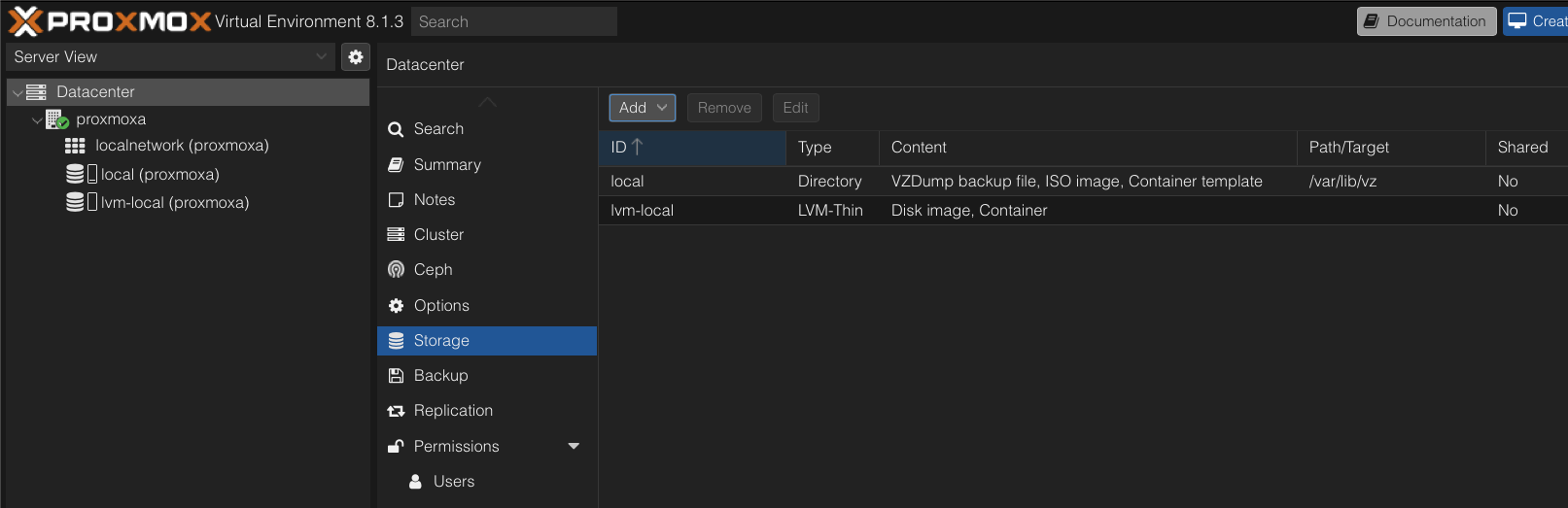
There are several ways you can add additional hard drives
